Friday, August 30, 2013
VMworld Wednesday Lessons Learned

Wednesday, August 28, 2013
VMworld Tuesday Lessons Learned
4. What is DevOps all about?
Cloud Consumers want the following, and these are driving network virtualization:
- Ability to deploy apps at scale and with little preplanning (provisioning speed and efficiency)
- Mobility to move workloads between different geographies and providers (investment protection and choice)
- Flexibility to create more diverse architectures in a self service manner (rich L3-L7 network services)
- Management Plane = NSX Manager - programmatic web services api to define logical networks
- Control Plane = Control Cluster
- Clustered App runs on x86 servers, controls and manages 1000s of edge switching devices, does NOT sit in data plane
- Data Plane = OVS/NVS
- Open vSwitch (OVS) vmWare-led open source project
- NSX vSwitch (NVS) is a software vSwitch in ESXi kernel
- Switch software designed for remote control and tunneling installed in hypervisors, NSX gateways or hardware VTEP devices
- Can work with vSphere, KVM, XenServer
- vSwitch in each hypervisor controlled through API by Controller Cluster
- NSX manager uses this API, so does cloudstack, openstack, CMS/CMP, VMware
- To get between physical and virtual networks, Open vSwitch NSX Gateway or HW Partner VTEP Device is used
- NSX Controller Cluster establishes an overlay network
- Multiple tunneling protocols including STT, GRE, VXLAN
- Packets encapsulate with Logical Switch info
- The tunneling protocol is NOT network virtualization, rather, it is a component of it
- Automated network provisioning
- Inter rack or inter DC connectivity
- P2V and V2V migration
- Burst or migrate enterprise to cloud
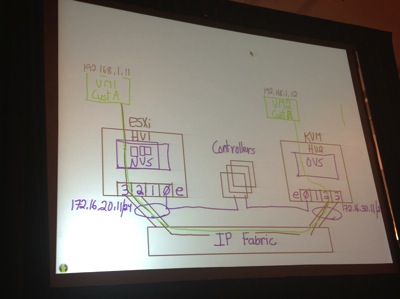
The Whiteboard snapshot above was drawn to demonstrate the basic components of NSX and how VMs communicate using the virtual overlay netowrk
The example uses ESXi on left and KVM hypervisor on right (HV1 and HV2)
- Each connected to IP fabric
- 3 controllers drawn in the middle
- Intelligent Edge NVS installed on ESXi and OVS installed on KVM
- Controllers talk with ESXi on vmkernel management interface, something similar with KVM
- Addresses assigned that used for encapsulation and direct communication between hypervisors: 172.16.20.11/24 on left, 172.16.30.11/24 on right
- Customer A is green, they have a VM on each hypervisor (192.168.1.11 on left, 192.168.1.12 on right)
- Customer B is red, they have VM on each hypervisor with SAME IP ADDRESSES - logically separated similar to VRFs (I didn't get a picture of this--sorry)
- Controller cluster controls virtual ports, so they can programmatically control QoS, Security, Distributed Routing
Tuesday, August 27, 2013
VMworld Monday Lessons Learned
Started out a productive day with my first-ever Fritatta and some delicious croissants at breakfast in Moscone South. Having seen the debacle of "breakfast" at last year's VMworld, the seating this year was at least an improvement with areas available in both Moscone South and West.
I went to the General Session at 9am, but as I was seated towards the back I couldn't see the bottom of the screens. There were no screens overhead, only 3 or 4 large screens up front. In addition, the vmworld2013 wireless SSID was nowhere to be seen. The Press SSID (vmwaremedia) was available but locked down. Attempts to use my AT&T MyFi were stifled due to the overwhelming RF interference in the area. And I had AT&T cell coverage but no throughput. Having seen how well wireless CAN be delivered at Cisco Live, even in this kind of space for 20,000+ people, I was very disappointed. I decided to go watch the Keynote from the Hang Space, but that was full to capacity with a line waiting to get in. I finally gave up and walked over to Moscone West, 3rd floor, and sat at a charging station watching the live stream while waiting for my first breakout session. (Kudos at least for the stream working.)
My first session was "Moving Enterprise Application Dev/Test to VMware’s internal Private Cloud -- Operations Transformation (OPT5194)." This was a great story of how leadership from the top pushed VMware to implement Infrastructure as a Service (IaaS). Kurt Milne (@kurtmilne) (VMware Director of CloudOps) and Venkat Gopalakrishnan (VMware Director of IT) shared lessons learned during VMware's internal implementation of a service catalog and the automation of processes which used to require manual intervention by cross-functional teams over the course of weeks. The process of standing up a new Software Development Life Cycle (SDLC) series of dev/test/uat/stage/prod environments has been greatly automated and provisioning time reduced from 4 weeks to 36 hours and they plan to reduce it to 24 hours in the near future. If you're going through a similar journey in your organization, this session is a must see when recordings and slides are released after the conference. I believe the session was also live-tweeted by @vmwarecloudops.
The other session I attended today was the very popular "What's New in VMware vSphere" presented by Mike Adams (http://blogs.vmware.com/vsphere/author/madams). We reviewed some of the new features released in vSphere 5.1 last year as well as some of the changes made for vSphere 5.5 this year. Some key takeaways for me (your mileage may vary):
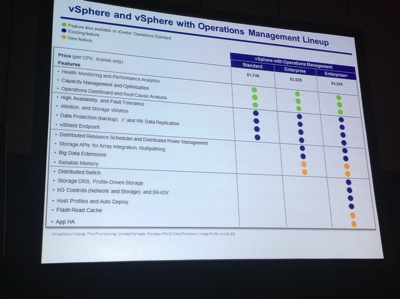
- vSphere is now wrapped up with Operations Management, i.e., vCenter Operations Manager (vCOPS). Referred to as "vSphere with Operations Management" it's now available in the Standard, Enterprise, and Enterprise+ flavors, each of which includes vCOPS Standard. See snapshot of feature breakout and license cost.
- vCloud Suite variations all include vSphere Enterprise+, vCloud Director (vCD), and vCloud Networking and Security (vCNS). The individual flavors depend on the version of vCOPS and vCloud Automation Center (vCAC) which are Standard, Advanced, and Enterprise. In addition, the Enterprise SKU also includes vCenter Site Recovery Manager (vC SRM).
- vSphere Web Client is replacing vSphere Windows Client, so we "better get comfortable with it." If I understand correctly, vSphere 5.5 includes support for all functionality in the Web Client now but not the Windows Client.
- New features in vSphere 5.5 include: VMDK file support up to 62TB, 4TB memory per host, 4096 vCPUs per host.
- vSphere Replication allows full copying of workloads, including the VMFS files, without shared storage. This perhaps saves the cost of more expensive synchronous or asynchronous storage replication, but has a somewhat limited Recovery Point Objective (RPO) of about 15 minutes. Still, this may be a good fit for some organizations for DR (including mine).
In addition to the sessions I was able to complete three labs (between yesterday and today) all related to VMware's recently announced vCloud Hybrid Service (vCHS). HOL-HBD-1301, HOL-HBD-1302, and HOL-HBD-1303 give a good introduction to the components and steps necessary to migrate workloads from a vSphere or vCloud Director environment in your own datacenter to the vCHS environment, as well as networking & security components and managing the service.
One big announcement during the morning General Session/Keynote was the release of VMware's network virtualization product called NSX. This is the marriage of Nicira (an earlier VMware acquisition) and vCNS/vShield in a new product. As a network engineer by background and training, this is particularly interesting to me. I was able to start the NSX lab (HOL-SDC-1303) but couldn't yet finish as I ran out of time. I plan to finish tomorrow. More to come on that.
I have to give a big thumbs-down to VMworld's requirement that we all get our badges scanned as we enter lunch. I don't remember this last year, nor have I ever seen this at any other conference I've attended. What gives? It's hard to hold a herd of hungry humans back from the food!
Finally, I visited with some fine folks at the Rackspace booth in the Solutions Exchange, including Waqas Makhdum (@waqasmakhdum). I now understand that Rackspace's Openstack platform uses a different hypervisor solution than VMware or Amazon EC2, but they offer guaranteed uptime with a phone number to call for support and apparently pretty reasonable costs for running a VM you control or even hosting the VM and just having you run your application on it. Also, I learned they offer VMware-based Managed Virtualization to allow you to "Set up a single-tenant VMware environment at our data center, rapidly provision VMs, and retain full control using the orchestration tools you’re familiar with." (Ref: http://www.rackspace.com/managed-virtualization/)
I'm failing to mention all the great people I met and conversations but one would expect nothing less from a great conference!
Sunday, August 25, 2013
Swack's VMworld To-Do List
It's time for VMware's 10th Annual VMworld conference in beautiful San Francisco! This is my second trip to VMworld and I'm looking forward to making it my best one yet. As such, I'd like to share some of my goals for this week. I feel that publishing my objects tend to keep me motivated.
1. Gain better understanding of NSX (came from vCNS/vShield and Nicira) and dive more into details of VMware networking
2. Better understand OpenStack and maybe take a test drive
3. Learn some basic functions of PowerCLI
4. What is DevOps all about?
5. Set up vCloud Director and/or vCenter Orchestrator and try it out
6. Learn about VMware's Internal Private Cloud for dev/test workloads
7. What is Cloud Foundry and how does it relate to my company?
If you have insights or can point me in the right direction please do! Comment below or find me on Twitter (@swackhap).
-Swack
Tuesday, June 25, 2013
Cisco Live Tuesday Lessons Learned
- EIGRP is no longer proprietary. Cisco has published an IETF Open-EIGRP Informational Draft. This means other companies can now implement EIGRP into their products if/when customers demand it.
- Neighbor authentication done with MD5 is no longer secure enough, so they've implemented SHA2-256 Hash-based Message Authentication Code (HMAC) to protect EIGRP messages exchanged between routers.
- The advent of 10Gbps links made it necessary to change the formula used to compute EIGRP metrics, now referred to as Wide Metric Support. They mentioned this was supported as of EIGRP release 8 and that the "show eigrp plugin" command would show version, but I tried on an NXOS and IOS router in my network and those commands didn't seem valid.
- How many of us enterprise customers use EIGRP in the LAN and have to redistribute with BGP for MPLS circuits? The problems inherent in this redistribution (which I have personally experienced, sometimes painfully) led them to create a new feature called Over the ToP (OTP) which uses LISP to bridge two EIGRP-speaking "CE" routers across a provider's MPLS cloud. One of the CE routers acts as a "route reflector" (term stolen from BGP) to consolidate route sharing amongst multiple CE routers connected to the MPLS cloud. OTP is shipping this month or next for IOS XE, then IOS in November.
Saturday, June 1, 2013
VMware View Problems with 64-bit Windows 7 Virtual Desktop
We've been growing our Virtual Desktop Infrastructure (VDI) quite a bit lately, and as a result I've taken ownership of a shiny new Windows 7 64-bit virtual desktop. Unlike the 32-bit Win7 VM I used before, though, this one has been giving me trouble.
The trouble starts when I am trying to reconnect to the already booted VM from a machine other than the last one I was on. Specifically, I use Windows 8 64-bit at work on a Dell tower with 4 monitors (two dual-monitor graphics cards). I use my VDI VM all the time from that machine on all four monitors. I also have a Macbook Pro (MBP) that I take to meetings and use outside the office.
Sometimes (not always) when I re-connect to my VM from my MBP I get a black screen with a mouse cursor and nothing else. After waiting a minute, I either disconnect or quit the View application and re-launch. Reconnecting the second time gives me an error indicating that desktop resources are busy. When this happens I cannot even connect via RDP, let alone through the usual way via the View broker. I attempt to restart the guest OS through vCenter but it never actually reboots unless I power cycle the VM in vCenter.
I worked with VMware Support but unfortunately haven't been able to fully solve the problem. The View support folks have looked thoroughly at our setup and don't see anything that could be causing problems. They handed me off to another group that was able to analyze a crash dump of my VM after the problem occurred, but they could only tell me that it appeared the VM was trying to use 3D rendering services of some sort (if I remember correctly).
As a workaround, I now re-size my View window on my desktop before disconnecting so it is intentionally smaller than the laptop from which I usually connect. This seems to have helped but it's rather frustrating. No other users have reported having the same issue, but there are currently no other VDI users with more than 2 screens. I should also point out that I've observed the same behavior when I connect from my home Windows 7 machine. It doesn't seem to matter if I'm connecting to the internal View servers that only use AD authentication or if I use the Secure Gateway View server that requires 2-factor authentication and tunnels secure PCoIP.
Based on all the evidence it seems my problem is related to having 4 monitors, but VMware support has been unable to identify the root cause and neither have I. If you have ideas, I'd love to hear them. Hit me up on Twitter (@swackhap).
Sunday, August 26, 2012
VMworld Hands-On Labs, Follow-Up
In case you hadn't heard, VMworld became "VMwait" today as I, along with quite a few other strong-willed geeks, waited well over seven (yes, that's SEVEN) hours before being seated for our first Hands-On Lab (HoL). Despite the hardships sustained by all, including the folks in green shirts running the labs, we all came through it alive and stronger for it. To make it up to us, they decided to stay open until 10pm at which time no new folks could enter but those of us that were there could finish what we started. Proudly, I managed to get three labs in (at least most of them) before heading back to my hotel for the night (sorry v0dgeball and VMunderground, I couldn't make it…maybe next year). Unfortunately, I heard some labs were still having problems even once they got the environment up and running. But luckily for me, I had fairly minimal issues and was able to learn lots!
I want to give a HUGE shout-out to Mr. Irish Spring who did an outstanding job listening to our feedback today and made sure we were supplied with refreshments when we got hungry and kept us informed.
Also many thanks to Ms. Jennifer Galvin who spent some time chatting with some of us, listening to our (mostly justifiable) grumbling about the experiences of the day.
In all fairness to VMware, I understand that some of the back-side tech being used this year is different than last year (indeed, some of it isn't even being announced until Monday morning's keynote). They took a risk and ended up having some problems. It's certainly happened to me. I'm betting it has (or will) happen to you.
Hopefully tomorrow will be a better day for everyone involved with the labs.
VMworld Hands-On Labs, First Look
My Sunday here at VMworld began with a good breakfast at a local bakery. I then headed to Moscone West shortly before the Hands-On Labs (HoL) were scheduled to open at 11am and was greeted with this scene:
I was able to navigate through the Traditional HoL crowd to the slightly shorter Bring Your Own Device (BYOD) line, indicated by this nice guy:
After the doors opened, I followed the line inside to the BYOD Check-In Desk. While in line, some very helpful green-shirted VMware folks explained how to prepare our machines for the HoL. After handing over my conference badge to the folks at the table, they entered me into the system and I proceeded to the BYOD Configuration Desk across the room:
I'd decided to take someone else's advice and use my iPad to login to the http://vmwarecloud.com site from the HOL wifi (only available inside the HoL area). That way I can access the lab guide instructions on my tablet and then I could use my MacBook Pro to connect to the lab environment with the View Client. The waiting continued in the "Holding Tank" where I hung out with about 100 other folks waiting for my name to proceed up to the top of this screen:
While waiting, they had a small seating area set up where the folks that wrote the labs were presenting whiteboard sessions:
Once my name reached the top of the screen I headed to the Seating Desk where I obtained my password and access code to login to the HoL site.
With this single-use code in hand I was guided to the BYOD HoL seating area where I set up to do my first lab! Based on what I've heard from previous VMworlds, I think it'll all be worth the wait.
Saturday, August 25, 2012
VMworld 2012, Day 1
I'll admit it. I'm a newbie to VMworld. Yes, this is my first time. But I've been to a few Cisco Live conferences (about 10 I think) so I've been eager to experience VMworld!
I arrived at the San Francisco airport (SFO) this afternoon after a pleasant day of flying from St. Louis, and caught a cab to my hotel. FYI, it was about $50 and 25 minutes to the Westin at 3rd and Market. After checking into the hotel, I walked a couple blocks to Moscone South to check into the conference.
Self Check-In had numerous Dell laptops prompting to enter first and last names. It then found me in the system and re-prompted for my first name (I assume in case I wanted to use a nickname). I hit submit and it told me which line number to stand in to pick up my badge and lanyard.
SECURITY NOTE: I'm concerned that they didn't ask to see my ID when they gave me my badge. This has been standard procedure at Cisco Live for years and I hope they just slipped up with it being the first day.
[Follow-up: I heard back from several folks on the VMworld Help group in the SocialCast conference community site. They ARE supposed to ask for ID and VMworld staff will address this with registration folks.]
With badge in hand (or rather, around my neck), I found out I had to head to Moscone West for Materials Pickup. (Side note: I'm looking forward to getting lots of walking in this week!)
Entering Moscone West you get this scene. Note that Self Check-in is available in Moscone South AND West locations.
I decided to check out the wireless so connected to the "VMworld 2012" SSID on my iPhone. I tried browsing somewhere as a test, and a splash page popped up with a vendor advertisement (yawn) with a countdown timer ("5 seconds until launch"). However, the first time I tried it showed me this weird login screen:
I walked over to the Technical Support desk near the Southeast entrance and asked about it. They indicated that it acted weird like that and I should try it again. When I did, voila, I got connected and it immediately directed me to the VMworld Mobile website (which I had already logged into earlier in the day).
Having completed my mission for the day, I headed back to the hotel to do the "Backpack Unboxing" and take some photos, shared for you below. I'm very excited to be here and grateful for the beautiful weather (it was about 67F when I arrived this afternoon).
Hit me up on Twitter (@swackhap) with your comments or questions, or leave a note below.